A major vulnerability was found in Contact form 7 that makes the attacker patch and upload malicious script on sites.
A vulnerability was discovered in contact form 7 that allows attackers to upload unwanted scripts. The publisher of contact form 7 has released an update to fix the vulnerability.
Unwanted File upload Vulnerability
The unwanted file upload vulnerability for WordPress is when the installed plugin in the website allows attackers to upload the malicious script to harm the website and get benefited without the permission of the website owner.
A malicious script is also known as a web shell that attackers write using web coding after get uploaded to a vulnerable site, attackers can gain access to the website, change the functionality, and tamper with the database. Contact Form 7 release their latest update as an “urgent security and maintenance release.”
“An unrestricted file upload vulnerability has been found in Contact Form 7 5.3.1 and older versions.
Utilizing this vulnerability, a form submitter can bypass Contact Form 7’s filename sanitization, and upload a file which can be executed as a script file on the host server.”
More detail and information bout the vulnerability is provided on Contact Form 7 on WordPress respiratory page. There is some additional information about the vulnerability of the plugin.
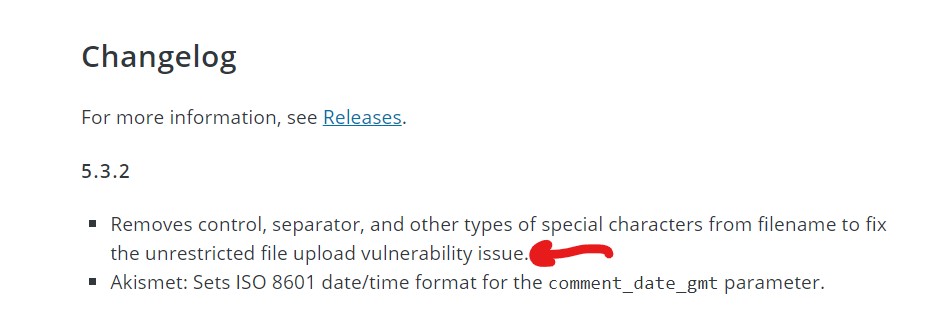
Removes control, separator, and other types of special characters from filename to fix the unrestricted file upload vulnerability issue.
Akismet: Sets ISO 8601 date/time format for the comment_date_gmt parameter.
Contact Form 7’s filename sanitization
Filename Sanitation is the indication of a function related to the web script that processes uploads. This function organizes and control the file for upload and restricting other kinds of file. It also controls the path of the file. The system of file sanitization works by restricting certain files name or also can allow a restricted set of file names.
In Contact Form 7, the issue was in filename sanitization in which created a situation that allows a certain kind of dangerous file unintentionally.
WordPress Plugin Changelog Update Description Screenshot
The above capture is from the Contact form 7 plugin in the development tab you scroll down into Changelog when you install that WordPress plugin. The same thing published on the official WordPress repository for plugins.
Vulnerability Fixed in v5.3.2 of Contact Form 7 Version
The vulnerability First time was discovered by researchers at Web Security company Astra. The filename sanitation vulnerability is completely fixed in Contact Form 7 version 5.3.2. All the versions below 5.3.2 are considered to be vulnerable should immediately get an update.